
Black hat techniques are considered as the dark technique for SEO because it does not give you long lasting results. But then also these techniques are employed by many for targeting their content on a high scale, even if it does not give you a promising long results.
Want to know more about all 3 SEO techniques?
These black hat techniques were a boom few years back, at that time Google was not smart enough to tackle these black hat SEO techniques and thus it was really easy for someone to rank there website higher in search engines.
Here we are going to discuss those techniques that are very popular among black hat community.
Before that let us know?
Why Black Hat Techniques Are Needed And Why They Are Banned?

Black hat techniques are mainly used by people or web masters who want to rank their websites at a good position in Google or in any of the search engines in spite of the fact that the fruit they are going to reap will not last longer. Obviously, these are unethical techniques which affect the user experience that is why it has been banned by major search engines. Then also these techniques are widely used and implemented on million of websites daily.
When these are banned why people still love them?
These types of question arises in one’s mind when they are reading about this unethical way of ranking on Google and they also think what is the use when it is going to get ban.
OK, so let me explain you with a help of an example here.
Let us say that you have a software company which has just launched new software. You want that new product to be marketed massively and want to get a good handsome amount of money. Getting more specified to the product. Let us assume it’s a computer cleaning software named “xyz” which is new to the market and it costs around $10. If using a simple Black hat technique of creating website for that specific product only and proving that website with hell lot of back links which may be irrelevant as well can give you a broad business obviously. Because the more you reach, the more is probability for the goal achievement.
Likewise there are 1000’s of places where you might need such black hat techniques which give boost to your website or business. Though you are not going to be in WWW for long but, then also you can go beyond the sales which you made without them.
So, May we just move further and know which all techniques are referred to as black hat SEO techniques.
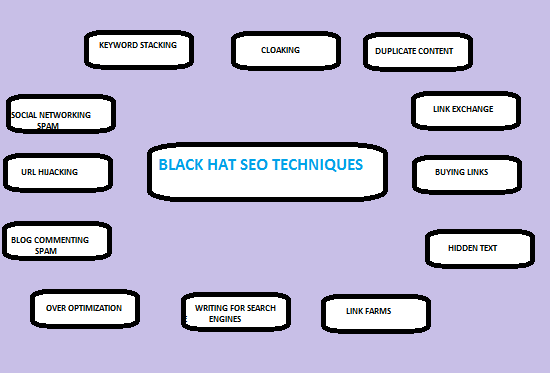
What All Techniques Fall Under Black Hat Techniques?

So, here we are going to discuss about the techniques that are used widely as Black hat techniques.
But after the new update of Penguin 4.0, it is really hard to get through some of the techniques easily.
Anyways here they are:
- Cloaking: Cloaking is a black hat technique, which have a sole purpose of showing different url’s or content to the user and search engines. In this manner any user coming on the search engine result page, looking for some different content but redirected to different content. This technique is used to manipulate search engines and used by so many geeks over the internet for their benefit. This technique violates the Google webmaster guidelines hence it is totally banned on search engines.
- Content automation: Content automation is a technique of generating content that too with the help of tools or any software. These types of practices are not considered as any kind of help to the user or automated content also does not designed in a manner to understand the concern of the person. Content automation software is not bothered about any kind quality for the end user. Since Google and other search engines are very much focused on quality so they don’t allow these websites to rank on them.
- Keyword stuffing: Keyword stuffing means filling your content with keywords where there is no need of them. It is basically done to manipulate search engine indexing and ranking. Adding variations of keywords at unnecessary places creates a bad impact on the reader’s mind and he may not return to your website. Thus keywords should be added to relevant places and content must be optimized according to yoast SEO.
- Hidden text or links: The type of activities in which texts or links are made to hide behind any picture (In this manner if someone clicks on the image they will be redirected to the link address). Hiding text or links can also be done by writing text in pure white on a white background. This black hat technique will work for link formation or for providing back links.
- Sneaky redirects: This is a bad bad black hat technique which is banned by Google far way back. Redirecting a user to some other website or URL can be beneficial when it comes to the maintenance of a page. When such things happen then redirection codes are employed to divert your customer to other address. But when you are fooling search engines and showing their crawlers something else while your user is redirected to some other address which he has no Idea about. Sometimes while you are on desktop the same website will work absolutely great but at the same time when you are operating it through mobile device, it redirects you to some other website.
- Link farms, Link wheels and link networks: Link manipulation is a method of creating unnecessary links by some unethical means. Unethical means refers to the techniques like link schemes, link farming etc. These techniques are purely considered as Black hat search engine optimization technique. Link farming can be done by creating one or two websites that have a sole purpose of creating back links to other websites. Link wheel is a strategy of passing link to link within two websites or among different websites for creating a link structure that would also pass the value of the website. Link network is yet another link generation method in which 2 or more websites are made to back link with main website. These websites are mainly governed by same person who is in need of back links; it has nothing to do with user experience and hence, only meant to manipulate search engines for getting high page ranking.
So, we hope that you got to know a lot more about Black hat techniques and why not to use them, from this article.

